

Why IoT Device Certification is a
The problem with poorly designed devices
IoT is on a roll. By 2025, it’s estimated that 152,200 IoT devices will be connecting to the internet every minute and the number of connected IoT devices will reach nearly 31 billion.
It’s well known that IoT can improve efficiency, productivity, and quality of life in many areas from smart homes, health, and remote working to industry, factories, and retail. It’s also well known that not all IoT is life enhancing (or even moderately helpful). But aside from devices that don’t work well or are connected just for the sake of it, some IoT devices can cause serious problems on mobile networks. And deployments of hundreds of thousands of these devices can be catastrophic, even bringing networks down.
This paper describes the problems that poorly designed IoT devices can cause on mobile networks, how standards and certifications can help all players in IoT, and how to address these requirements efficiently.

The dark side of IoT
A network fault or incorrectly configured parameter might stop a device from connecting to a network. If it’s not designed correctly, the device might attempt to connect repeatedly and never give up. Replicated in many thousands of devices using the same network, this behaviour could escalate into an unstoppable loop, causing increasing numbers of other devices to fail. Signalling overload can severely impact the network and cause cell congestion or widespread disruption. In the worst case, the problems could disable an entire network.
Inefficient connectivity behaviour also impacts the devices themselves. Connecting to a network uses power, so repeated connection requests can reduce battery life. Similarly, excessive read and write cycles can reduce the lifetime of a SIM.
Security is another concern. Insecure devices can be compromised, recruited into vast botnets to use in DDoS (Distributed Denial of Service) attacks. Hackers can gain unauthorised access to business and consumer data or run up vast charges through illegal use.
Network operators have a responsibility to provide high quality service to all their users and must balance their resources between signalling and traffic requirements. Unexpected signalling demands from poorly designed IoT devices can have a detrimental effect on service quality both for the IoT service itself and for other cellular connectivity users.
Punishing problem devices
Network operators can use certain mechanisms if they need to protect other devices and users from suffering adverse impacts caused by IoT devices. They can, for example
- Use a SIM toolkit application to detect repeated device reboots and aggressive network connection reattempts and disable network credentials for a period of time.
- Use dynamic billing to charge different amounts at different times of the day to discourage mass synchronised behaviour, such as over-the-air updates, at peak times.
- Detect abnormally high levels of signalling or data load on the network and temporarily disable subscriptions if it is (or might) impact the performance of the network and other users. If necessary, a problem device may be permanently disabled.
While operators only use these mechanisms as a last resort, it’s better to ensure there’s no risk of your IoT devices suffering this fate.
Inefficient connectivity behaviour also impacts the devices themselves."
Certification can help
Standards and certification bring order to an unruly world and provide the framework for all IoT players to operate successfully together.
Regulatory certification
Many countries and regions require electronics products to comply with regulatory standards before the products can be sold in specific markets. These standards cover aspects such as electrical safety, Radio Frequency (RF) emissions interference, electromagnetic compatibility, and environmental factors.
Examples of regulations include:
- China Compulsory Certification (CCC)
- Electromagnetic Compatibility (EMC) Directive 2014/30/EU and Radio Equipment Directive (RED) 2014/53/EU
- Federal Communications Commission (FCC) Part 18
- Gijyutsu Kijyun Tekigō Shōmei (Giteki)
- Network Access License (NAL)
Industry certification
Different industries may require products to conform to specific standards for each industry. The telecoms industry has two main certification schemes for mobile devices, which are based on 3GPP standards, SIM functionality and antenna performance:
- Global Certification Forum (GCF) is a worldwide, voluntary scheme that uses self-declaration with a quality assurance and certification challenge process. Devices without certification may be blocked from connecting to GCF members’ networks.
- PTCRB is mainly used in North America and is mandatory for devices using PTCRB members’ networks. Devices without this certification may be blocked. Each PTCRB certification is verified with tests executed at PTCRB approved labs.
Network operators often require one of these certification schemes to be obtained as part of their acceptance or certification requirements.
Vertical industries, such as automotive and medical, may have additional certification schemes that apply to IoT devices that operate in their target markets. They can cover end user safety and other specific requirements, such as extreme operating temperatures and vibrations.
Operator certification
Some mobile network operators use their own testing and certification schemes, which may be in addition to industry certification.
Operator schemes ensure device interoperability specific to their network configuration and network parameter settings. They can test in-field performance, such as radio sensitivity, dropped connection rate, handover success, data throughput and battery life. Testing of devices using newer technologies, such as LTE-M, NB-IoT and 5G, can be used to ensure the devices are customised properly to benefit from the specific network configurations required.
Operators use their own certification schemes to minimise connectivity issues and ensure that devices on their network don’t have an adverse impact on the network or other users. They typically perform rigorous testing on white-labelled devices to ensure the devices work as intended and don’t create ongoing issues for customer support teams.
Note on roaming
Operator certification is often only needed on the local (home) network and not for any networks that the devices may roam onto. However, roaming presents other pitfalls and long-term consequences for IoT devices, so it’s better to ensure devices are not reliant on permanent roaming. Read about how to resolve permanent roaming issues.

Understanding the certification challenges for IoT
The smartphone industry is well advanced along the learning curve for operating successfully with mobile networks. Working together, network operators, smartphone manufacturers, and application developers have used standardisation, technology developments, and improved applications to resolve the initial difficulties.
IoT device manufacturers and service providers now need to go through the same process with the network operators.
But IoT has some crucial differences to the smartphone industry:
- IoT devices are typically simple devices without the capacity to run sophisticated software or have any user intervention, making it harder to include the same levels of security and connectivity functionality as smartphones.
- There are many more players in the IoT industry and different commercial and operating models. Network operators are less able to influence the behaviour of manufacturers and application developers.
- IoT devices, particularly Low Power Wide Area (LPWA) devices, tend to be price sensitive, so IoT service providers can find it challenging to fund the costs of additional work such as running field trials and certifying devices.
IoT certification affects many parties, including mobile network operators, IoT service providers, manufacturers of devices and communications components, and application developers.
The next section describes the architecture of an IoT device to show what’s involved with IoT connectivity.
Low Power Wide Area (LPWA) Definition: Wireless technologies for IoT that enable low-power, long-range, and cost-effective connectivity, ideal for devices transmitting small data over extended distances.
IoT device architecture
The diagram below shows a generic IoT device architecture based on a GSMA representation6 and focused on connectivity.
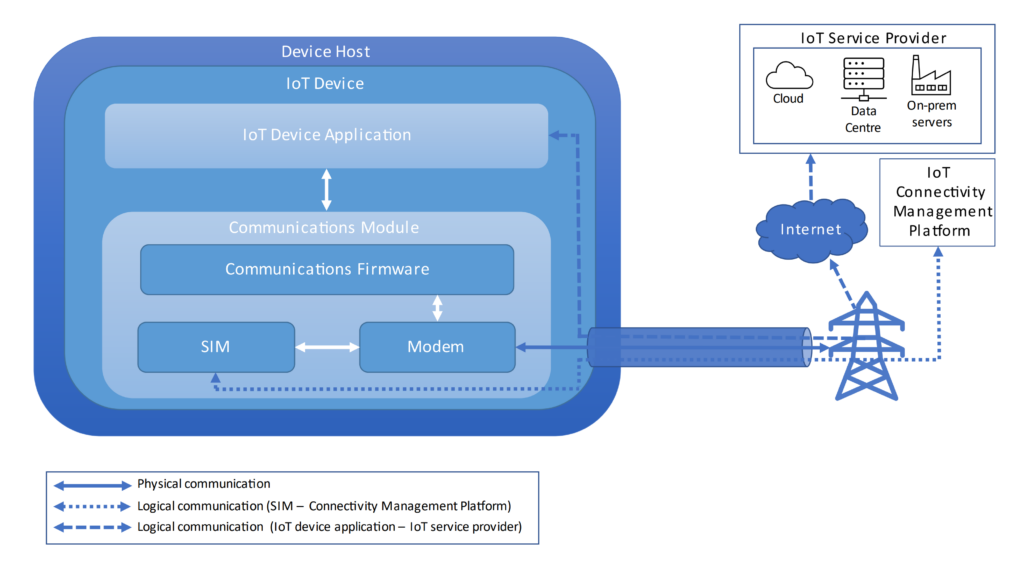
The IoT device is the equipment that performs the IoT operations, for example, making a drink in a vending machine or collecting a water meter reading. As well as the machinery or electronics to perform its tasks, the IoT device contains a number of components:
- The IoT device application controls how the device performs. It’s responsible for connectivity and data transfer with the IoT service provider system and responds to instructions received from the backend system.
- The communications module performs the connectivity for the device. Within the module:
- The communications firmware provides an API for the IoT device application to use to manage connections and data transfer. The firmware instructs the modem when to connect to the network.
- The modem (which includes the radio baseband chipset) performs the radio communications with the mobile networks. Modems can have the ability to connect to different types of network, both cellular (2G, 3G, LTE) and other types (such as Wi-Fi and Bluetooth). For cellular connectivity, the modem connects to the network presented to it by the SIM.
- The SIM (UICC or eUICC) securely stores the subscriber, authentication, and network profile data. More sophisticated SIMs store multiple network profiles for improved coverage and resilience. They determine the preferred network for the modem to connect to depending on factors such as location and network quality. The SIM works with an IoT Connectivity Management Platform (CMP) to provide optimum connectivity for the device.
Connection efficiency guidelines
The GSMA IoT Device Connection Efficiency Guidelines provide comprehensive guidance on the requirements for each player in the IoT ecosystem to ensure that mobile networks can provide all users with a high-quality service.
The function of the device determines its behaviour, including how much data it needs to send and how often it needs to send it. However, the device must always behave in a way that is considerate to other network users. Device manufacturers and application developers need to work together to design IoT devices that meet best practices and conform to relevant standards.
Examples of guidelines include:
Connection and data transfer efficiency
- Aggregate and compress data before sending.
- Keep the connection open if the device needs to send frequent messages.
- Close the connection between messages if they’re sent infrequently.
- Use low power mode when possible to reduce power consumption and signalling load.
- Monitor and manage factors such as the number of connections, connection quality, data transfer speed, and amount of data sent.
Network behaviour
- Avoid synchronised behaviour for network connections particularly for devices in large deployments (for example, use a randomised delay for connections and over-the-air updates).
- Conform to operator guidelines for management functions like keep alive, dynamic polling, preferred usage times.
Security
- Follow standard security guidelines (for example, IETF, W3C, OMA).
- Authenticate with the network when connecting.
- Prevent unauthorised or insecure device management functionality of software and firmware (for example, during diagnostics or over-the-air updates).
- Use end-to-end encryption.
Device behaviour
- Handle network failures gracefully, implement retry and reset mechanisms carefully (for example, don’t retry connections indefinitely and don’t reset the device too frequently).
- Don’t ping-pong rapidly between different communication access technologies (for example, using a fallback cellular connection if Wi-Fi fails) but allow time for temporary issues to resolve themselves.
- Report power outages or battery power problems to the service provider
Standards
- Certify with GCF or PTCRB as appropriate.
- Ensure compliance with 3GPP standards for mobile broadband.
- Ensure compliance with industry specific standards.
- Meet additional standards when required, for example, for IPv6 and eUICC.
- Meet mobile operator requirements for target market, gaining certification if necessary.
Testing and certification benefits all IoT players
The requirements for IoT device testing and certification can place a significant time and cost burden on enterprises wanting to bring an IoT service to market and can even become a barrier to entry in some vertical market segments.
Network operators, however, have a duty to ensure that they offer a quality service to all their users. They must prevent the adverse behaviour of some devices from degrading the experience for others. Operators with the most stringent levels of testing and certification tend to have the best performing networks, making them attractive to enterprises who want to deploy business-critical services.
Realising the benefits
Taking a proactive approach to implementing best practices for IoT connectivity means that an enterprise can monitor their own device performance and address issues without incurring punitive actions from the network operators.
Well-designed IoT devices provide the best experience to end users and enable enterprises to spend more on the business aspects of their IoT service rather than worrying that devices might lose connectivity at any time.
- Understand your target market and the requirements that this will impose on your IoT devices.
- Where possible, use certified components, such as modems and modules, to save time and cost.
- Work with expert partners who can guide you through the complicated regulatory and certification requirements so you can meet your obligations as efficiently as possible and succeed with your IoT plans.


